Understanding OMS Cyber: A Comprehensive Guide
OMS Cyber, an acronym for Order Management System Cybersecurity, is a critical aspect of modern business operations. As the digital landscape continues to evolve, protecting your order management system from cyber threats has become more important than ever. In this detailed guide, we will explore the various dimensions of OMS Cyber, including its significance, common threats, and best practices for securing your system.
What is OMS Cyber?
OMS Cyber refers to the cybersecurity measures implemented to safeguard an Order Management System (OMS) from unauthorized access, data breaches, and other cyber threats. An OMS is a software application that helps businesses manage their sales orders, inventory, and customer information. Given the sensitive nature of this data, it is crucial to ensure that your OMS is secure.
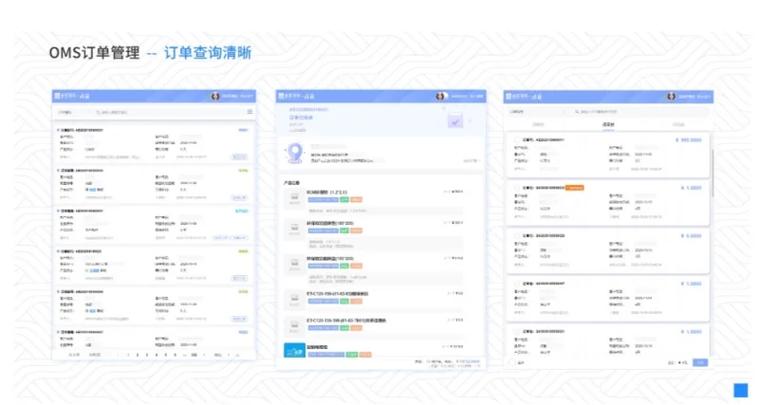
Significance of OMS Cybersecurity
Here are some key reasons why OMS Cybersecurity is essential:
| Reason | Description |
|---|---|
| Protecting Sensitive Data | OMS contains sensitive information, such as customer details, payment information, and inventory data. Ensuring its security is crucial to prevent data breaches. |
| Compliance with Regulations | Many industries are subject to regulations like GDPR and HIPAA, which require businesses to protect customer data. OMS Cybersecurity helps ensure compliance with these regulations. |
| Preventing Financial Loss | Cyber attacks on OMS can lead to financial loss due to theft of sensitive information, disrupted operations, and loss of customer trust. |
| Preserving Brand Reputation | A data breach can significantly damage a company’s reputation, leading to a loss of customers and business opportunities. |
Common Cyber Threats to OMS
Understanding the common cyber threats to your OMS is crucial for implementing effective security measures. Here are some of the most prevalent threats:
-
Malware Attacks: Malware, such as viruses, worms, and ransomware, can infect your OMS and compromise its integrity.
-
Phishing Attacks: Cybercriminals may use phishing emails to trick employees into providing sensitive information, such as login credentials.
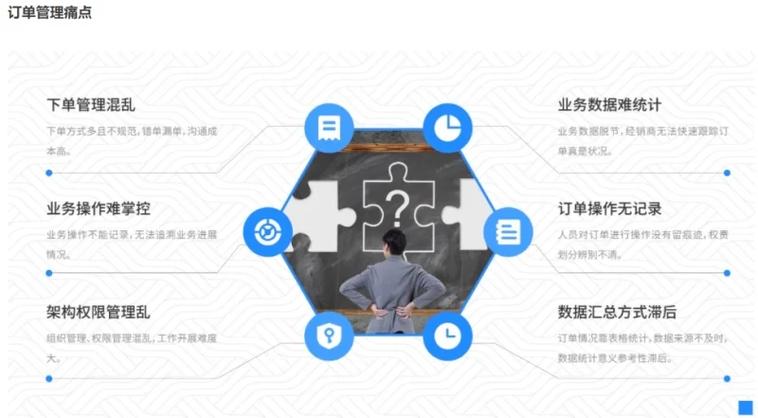
-
SQL Injection: Attackers can exploit vulnerabilities in your OMS to insert malicious SQL code, potentially leading to data breaches.
-
DDoS Attacks: Distributed Denial of Service (DDoS) attacks can overwhelm your OMS with traffic, rendering it inaccessible to legitimate users.
-
Insider Threats: Employees with authorized access to your OMS may misuse their privileges to steal or manipulate data.
Best Practices for OMS Cybersecurity
Implementing the following best practices can help protect your OMS from cyber threats:
-
Regularly Update and Patch Your OMS: Keep your OMS up to date with the latest security patches and updates to address vulnerabilities.
-
Use Strong Authentication and Authorization: Implement strong password policies, multi-factor authentication, and role-based access control to limit access to sensitive data.
-
Encrypt Data: Use encryption to protect sensitive data, both in transit and at rest.
-
Monitor and Log Activity: Regularly monitor your OMS for suspicious activity and review logs to detect and respond to potential threats.
-
Train Employees: Educate your employees on cybersecurity best practices and the importance of protecting sensitive data.
-
Backup Data: Regularly backup your OMS data to ensure that you can recover it in the event of a cyber attack.
Conclusion
OMS Cybersecurity is a critical aspect of modern business operations. By understanding the significance of OMS Cybersecurity, common threats, and best practices for securing your system, you can protect your business from cyber threats and ensure the integrity of your OMS.
